Use case 1
ANTONOV
In UC1 we are focusing on the cargo monitoring system designed by Antonov Company. The main purpose of this system is tracking and registering certain set of parameters in order to improve flight safety, and operational communication between the aircraft crew and ground personnel to increase the efficiency and profitability of commercial transportation of Antonov Airlines.
Obtaining data on cargo parameters can occur both after the aircraft lands at the destination airport by reading them from the SD card or laptop, and in real time using several approaches discussed in the next section.
The cargo monitoring system consists of the following main software and hardware elements as illustrated also in figure below :
- two digital pressure, humidity and temperature sensors,
- a computer with a recording device and a parameter indicator,
- a special program for monitoring parameters, installed on a laptop
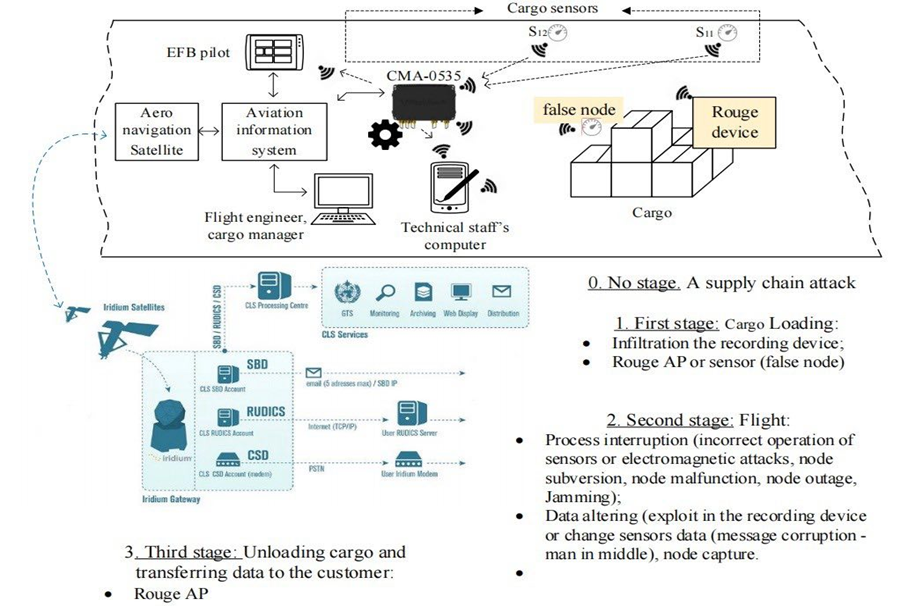
Flight cargo monitoring is a tool for effective management and analysis of processed flight information registered by the onboard flight data recorder, both during normal operation of the fleet and during investigations of flight accidents and incidents.
Providing secure and efficient access to information resources is an important component of the aircraft production process and its subsequent operation. Testing and optimization of access control systems to information resources will make the work of an airline company more efficient.
TELEMETRY will provide threat analysis and use anomaly and misuse detection, in components and systems to recognize hazardous conditions at component and system level. Also, TELEMETRY will identify vulnerabilities in access control to system components and will monitor the creation of temporary or permanent users with different access levels and sets of rights. TELEMETRY will also control typical or atypical behaviour, provide testing of response to incidents at the HW and SW level.
TELEMETRY tools can help improve the security of an air cargo monitoring system based on on-board indicators, information traffic analysis tools and anomaly detection.
From the perspective of possible scenario related to the IoT security of cargo aircraft. Two storylines are selected. The first scenario involves a rogue device and an unknown actor who interferes with the system and introduces a rogue sensor. The second scenario involves data being modified during transmission, which is consistent with the current practice of exporting CSV files. By using TELEMETRY tools, the aircraft’s information security system will be significantly improved by protecting the integrity of the data or risk reporting.
Currently, the TELEMETRY tools are being configured in terms of model training, issues of their interoperability and data exchange are being resolved, the sequence of operation of all tools is being determined, and scenarios are being refined. A clear architecture of TELEMETRY tools and information flows is at the testing and approval stage.
The first simulation results obtained with real flight data show the high quality of generalization of the developed machine learning models and high accuracy.


Use case 2
NOKIA
Smart factories are a heterogeneous entity consisting of many different individual components. Examples of these components are production machines and network components such as routers, IoT devices, and user devices such as laptops and computers that host software for controlling and operating the factory. As most of these components are “smart” and “online”, they are at risk of being attacked or becoming attackers themselves.
Examples of attacks on components are as follows:
- IoT devices whose outdated firmware enables an attacker to take over the device, or the manipulation of control data from production machines with the aim of damaging them or influencing product quality.
- Production machines that collect and send confidential operating parameters can themselves become an attacker. This can be initiated by an untrustworthy manufacturer, or by a legitimate firmware update that has already been compromised by an attacker at the manufacturer (“supply chain attack”).
- Devices that are introduced into the network without authorization (e.g., by a disgruntled employee) and launch cyber-attacks from within the network are another potential source of danger to the integrity and security of a smart factory.
Dangers and attacks as described above can already be countered today: Firewalls, rule-based traffic scanners or network segmentation are some of the most common measures with which network administrators try to contain risks of this kind, but these methods are mostly static and only defend against known or anticipated attack vectors. In addition, they must be manually maintained and expanded to be effective in the long term. To address this, TELEMETRY will investigate how to extend this approach with methods that attempt to recognize yet unknown variants of cyber-attacks through machine learning techniques. Specific examples of the approaches to be evaluated in this storyline are as follows:
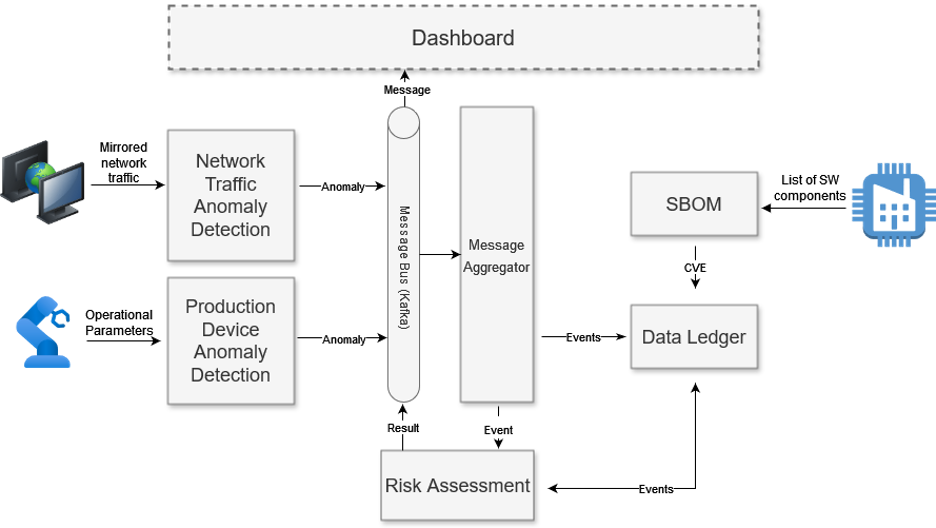
- Attacks on the production process are detected by analysing the operating parameters of a robot in real-time using a machine learning-based model and detecting anomalies in its operating behaviour.
- To detect covertly operating devices in the network, or to detect suspicious communication behaviour of known elements in the network, TELEMETRY will also use machine learning methods to detect anomalies in network traffic in real-time.
- A Software Bill Of Material (SBOM) of the network elements is regularly compared with the Common Vulnerabilities and Exposures (CVE) database to automatically provide the administrator with information on exploits.
- The central evaluation of the detected attacks and threats is carried out by a central risk assessment system, which collects the findings of the elements described and creates a final risk analysis for the smart factory.
- The result of this analysis, together with information on countermeasures, is then displayed to the administrator on the dashboard.


Use Case 3
TIM
Telecom Italia (TIM) is the incumbent telecommunications operator in Italy, providing both fixed and mobile data services to millions of subscribers. To ensure the cybersecurity of its devices before deployment in production environments, TIM needs to verify their robustness and reliability, with a specific focus on cybersecurity. In the context of the TELEMETRY project, TIM has developed a use case that replicates its real-world testing process. This testing environment accurately simulates a typical household or small enterprise network, including standard traffic patterns and volumes, though it does not involve actual users or home/business devices (Figure 8).


The primary focus of this use case is on domestic and small enterprise networks protected by Residential Gateway (RGW) devices (Figure 9). In this context, RGWs act as the interface between the telecom network and customer devices, such as PCs, servers, printers, smartphones, media systems, cameras, digital assistants, home automation platforms, and various types of sensors. Due to their strategic position at the boundary of these networks, RGWs are increasingly becoming targets for cyberattacks aimed at compromising the user’s domain or the telecom infrastructures.
As critical components, RGWs are vital to the telecom industry due to the large number of users they serve, the volume of data they handle, and the essential services they provide. However, IoT devices, including RGWs, pose significant challenges related to data governance, particularly in terms of privacy and security. If these challenges are not adequately addressed, they could introduce significant risks, compromising not only customer data but also the integrity and availability of the telecom provider’s critical infrastructure. Unchecked vulnerabilities may allow cybercriminals to exploit billions of IoT devices for malicious purposes, including Distributed Denial of Service (DDoS) attacks, phishing, data exfiltration, and privacy violations. Furthermore, these security weaknesses could expose the telecom networks to cyberattacks, disrupt essential services, and undermine customer trust, ultimately damaging the telecom provider’s reputation and business continuity.
Even worse, consumer- or small-business-grade devices, often designed with cost minimization in mind, are frequently deprioritized for ongoing maintenance and security updates. The drive to keep production costs low can limit the extent of security verification processes. To mitigate these risks, TIM has established a robust internal process to test RGWs for both known and unknown vulnerabilities, as well as misconfigurations, before deploying them to final customers. As part of this process, the TELEMETRY tools and framework will be integrated into TIM’s defined internal security testing procedures, with their performance and effectiveness being compared to existing commercial and open-source tools already in use.
